Few things are as sensitive – or as frequently targeted by cyberattacks – as financial data. Although banks and other financial service providers already implement extensive security measures, there remains room for improvement.
This need arises because the use of information and communication technologies (ICT) and digital networking continues to grow in the financial sector, requiring security measures that align with current regulations.
The key regulation addressing this is the Digital Operational Resilience Act (DORA). Designed to enhance and standardize cybersecurity and digital resilience in the financial sector, DORA establishes comprehensive IT security measures.
Discover the measures mandated by DORA, their applicability, and how LANCOM products can support your implementation and compliance on our DORA topic page.
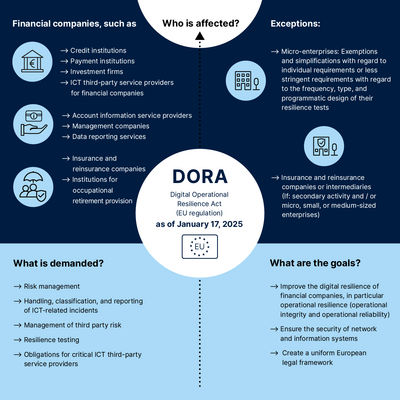
To whom does the DORA apply?
- Credit institutions
- Payment institutions
- Account information service providers
- Investment firms
- Management companies
- Data reporting services
- Insurance and reinsurance companies
- Institutions for occupational retirement provision
- ICT third-party service providers for financial companies
Exceptions:
- Insurance and reinsurance companies or intermediaries (If: secondary activity and / or micro, small, or medium-sized enterprises)
- Micro-enterprises: Exemptions and simplifications with regard to individual requirements or less stringent requirements with regard to the frequency, type, and programmatic design of their resilience tests
What does the DORA demand?
- Risk management (Chapter II, Articles 5-16)
- Handling, classification, and reporting of ICT-related incidents (Chapter III, Articles 17-23)
- Resilience testing (Chapter IV, Articles 24-27)
- Management of third party risk (Chapter V, Articles 28-30)
- Obligations for critical third-party ICT service providers (Chapter V, Articles 31-44)
How is implementation monitored?
National Supervisory Authority in Germany: The Federal Financial Supervisory Authority (BaFin), in collaboration with the Deutsche Bundesbank, oversees compliance within Germany.
EU Supervisory Authority: Credit institutions classified as significant are directly supervised by the European Central Bank (ECB).
Expected Consequences of Non-Compliance:
- Investigative powers: Authorities may conduct investigations, inspections, and question individuals or entities involved
- Corrective measures:Orders to implement corrective or remedial actions
- Penalties: Imposition of financial or other penalties
- Cease and desist orders:Mandates to cease operations or actions that violate regulations
- Criminal sanctions: Prosecution of serious violations under criminal law
- Public disclosure of sanctions: Details of sanctions, including the identity of the natural or legal person involved and the type of violation, will be published on the authorities' official websites
The legal requirements and framework of the Digital Operational Resilience Act (DORA) are causing concern for many financial companies and their service providers. What needs to be taken into account? What do the individual sections mean in practice? Few ICT service providers, system integrators, banks, or financial institutions are legal experts.
To address these concerns, LANCOM consulted two experienced lawyers from reuschlaw to provide an expert opinion and an informative FAQ on DORA. The result is a clearly written paper that presents all the essential information on DORA and answers the most common questions.
Feel free to access our exclusive, free white paper to gain comprehensive insights into DORA and ensure you're well prepared.
DORA implementation with LANCOM: Highest IT security for financial data
As a German full-range provider of network technology, we support financial companies and ICT service providers in the financial sector with GDPR-compliant, highly secure solutions. Our offerings include hardware, software, cloud control, and remote access infrastructure designed to help you implement the Digital Operational Resilience Act (DORA).
How do we achieve this? We’re happy to explain in the following section.
This is how LANCOM can decisively support a DORA-compliant overall solution
Find out here how LANCOM products and solutions can help you meet the individual requirements of DORA:

Risk management (Chapter II, Articles 5-16)
DORA requirements:
- Governance and control framework for ICT risks and the protection of hardware and software
- Processes for identifying, protecting, preventing, detecting, and responding to ICT risks
- Implementation effort must be proportionate to the respective risk
- Responsibility for implementation, management, and monitoring lies with the management of the financial company
LANCOM implementation and added value:
- 24/7 monitored network security and fast response times in an emergency thanks to system-wide security settings in the central management platform (LANCOM Management Cloud), incl. SIEM Integration Service
- Next-generation UTM firewalls with application management and deep packet inspection, content and packet filtering, anti-virus / anti-malware / anti-spam, intrusion detection / prevention system, and much more
- Central, transparent configuration of operating defaults for the entire network
- Redundancy and backup functions in core and distribution switches as well as in routers and gateways for maximum business continuity
- Cloud-controlled, fine-grained access rights assignment at application level according to the latest, highly secure zero-trust principle with LANCOM Trusted Access
- Regular, automatable software updates including feature updates, bug fixes, and security updates
- Transparent lifecycle management for long-term predictable firmware maintenance
- 100% backdoor-free and GDPR-compliant in all devices and software for maximum digital sovereignty

Handling, classification, and reporting of ICT-related incidents (Chapter III, Articles 17-23)
DORA requirements:
- Establishment of process for handling ICT-related incidents (coherent and integrated monitoring, root cause identification, and documentation)
- Definition of an “ICT-related incident” as an event not planned by the financial institution that affects the security of network and information systems and has a negative impact on the availability, authenticity, integrity, or confidentiality of payment-related data
- Classification according to the number of customers and transactions affected, the duration, the geographical spread, the economic impact, and the criticality of the services affected
- Obligation to report serious incidents to the authorities
LANCOM implementation and added value:
- Comprehensive and constant 24/7 network monitoring by the LANCOM Management Cloud (LMC) incl. real-time device status, easily analyzable dashboards, alerting functions and (security) reports
- Transparent security audit reports from the UTM firewalls on attempted attacks
- Simple integration of common security information and event management (SIEM) systems
- Automatic, proactive Wi-Fi anomaly detection in the LMC including troubleshooting tips
- Self-learning, automatic Wi-Fi optimization with LANCOM Active Radio Control™ 2.0

Management of third party risk (Chapter V, Articles 28-30)
DORA requirements:
- Develop a strategy for ICT third-party risk
- Maintain an up-to-date register of information on the nature and extent of use of all services provided by ICT third-party service providers
- Risk analysis prior to the conclusion of any such contractual agreement, e.g., appropriate information security standards or concentration risk (dependency-like exposure to service providers with critical consequences in the event of non-availability or deficits)
- Definition of minimum contractual requirements, e.g., for services, subcontracting, locations, data protection, quality of service, cost transparency, termination, etc.
LANCOM implementation and added value:
- Experienced, trained, and LANCOM-certified system house partners ensure DORA-compliant contracts at eye level
- LANCOM hardware and software includes extensive individual and independent configuration and maintenance options and is designed to empower our customers themselves in order to strengthen their digital sovereignty and reduce their dependence on service providers
- A wide range of training and education options for LANCOM solutions for more autonomy in everyday working life
- Maximum cost and software lifecycle transparency for optimal planning
- 100% GDPR compliance, backdoor freedom, and digital sovereignty

Obligations for critical ICT third-party service providers (Chapter V, Articles 31-44)
DORA requirements:
- Creation of a monitoring framework for critical ICT third-party service providers
- Classification mechanism for the type and extent of the financial sector's dependence on ICT third-party service providers
- Consideration of the lack of substitutability of the respective ICT third-party service providers
LANCOM implementation and added value:
- Tested NIS2 conformity of LANCOM products and solutions in the area of risk management
- Proven LANCOM mechanisms to strengthen resilience and crisis resistance, such as backup lines, active/active operation, and redundancy concepts
- Proven high security standards, e.g., through the German Federal Office for Information Security's IT security label and TeleTrust trust labels “IT Security Made in Germany” and “IT Security Made in EU”
LANCOM has been successfully implementing network infrastructure projects in collaboration with the financial sector for many years. Our firewalls, routers, switches, access points, and the LANCOM Management Cloud are already securing the networks of numerous banks and financial institutions.
Interested in learning more? Explore our latest references to gain deeper insights into our proven solutions!
Optimally protected finances
Customer data in the financial sector is some of the most sensitive information and is a coveted target for hackers. It is therefore all the more important to secure this data appropriately. For this reason, Otto M. Schröder Bank AG has modernized its branch Wi-Fi. With network-secure components without backdoors, content filters, and functions for high availability, the bank is optimally armed against network outages and cyberattacks. Thanks to the LANCOM Management Cloud, the changeover went smoothly without disrupting ongoing business operations.

Future-proof IT for Credit Unions
Ireland's St. Canice's Credit Union, with over 65,000 members, has modernized its outdated network to enhance security, scalability, and centralized management for the future. In collaboration with BITS and LANCOM, a resilient cloud-based solution was implemented using the LANCOM Management Cloud. This included centralized control, 24/7 monitoring, and proactive alerts.
The IT team can now respond more quickly, minimize downtime, and benefit from a robust, easy-to-manage, and scalable network infrastructure. Remarkably, the installation was completed seamlessly during ongoing operations.